|
Researchers are currently reporting a considerable upswing in the propagation of Zepto, the latest variant of the Locky crypto infection that got an abominable reputation as it had been causing problems to thousands of users worldwide
over the course of several months on end. The previous iterations and the new edition share a great deal of properties. First off, the spreading mechanism is the same: the ransomware operators are using a botnet to sustain a
bulk spam campaign. The phishing emails pretend to deliver copies of some important PDF documents enclosed in a ZIP archive. The offending code run instantly after a recipient opens the legit-looking attachment.
Another similarity with the predecessor is that the Zepto spinoff uses the same Command and Control infrastructure. However, before reaching out to the C2 server, it scans the breached system for various formats of files. The
infection has a hard-coded list of extensions, against which it checks all data residing on fixed drives, removable media and network disks. When the checkup and matching phase has been completed, the Trojan initiates a crypto
routine. To this end, it first scrambles files with AES algorithm. Then, it encrypts the 128-bit AES key using RSA, a stronger cryptographic system. Finally, the private RSA key is sent to the C&C server over a secure channel.
Ultimately, the files become unavailable after such processing.
In addition to that, Zepto badly tweaks filenames. It replaces them with cumbersome arrays of hexadecimal characters followed by the .zepto extension. The changes are so drastic that it appears impossible to link specific files
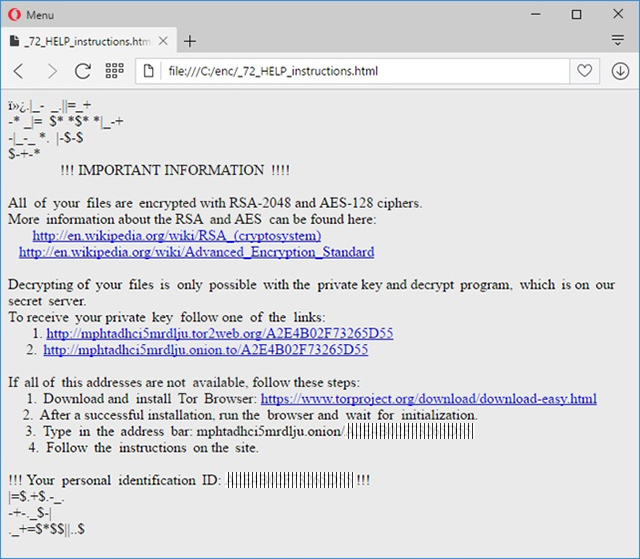
with their encrypted counterparts. At that point, the ransomware articulates its demands. It configures a _HELP_instructions.bmp image to be displayed as the desktop background. The message in it says, “All of your files are
encrypted with RSA-2048 and AES-128 ciphers. Decrypting of your files is only possible with the private key and decrypt program.”
The problem is that both the key and the automatic recovery solution are located on the criminals’ server. To obtain both of them, the victim needs to follow one of two links that are anonymous Tor gateways. On the “Locky Decryptor
Page”, the compromised person is expected to pay 0.5 Bitcoin ($336) for the decoding to become possible.
Instead of sending the ransom to the scammers, it’s highly recommended to use the steps below and check whether the workarounds can do the trick and restore the .zepto files to their original state.
How to recover .zepto files without submitting the ransom
A brief disclaimer: the techniques described below do not actually decrypt the locked data. Instead, they provide viable workarounds for exploiting probable imperfections of the way that this virus implements the crypto and handles
the victim’s files. Although it’s premature to assert whether or not these tips will do the trick in your situation, nothing more efficient has been invented to date. Without further ado, peruse the following methods to mitigate
the harm from the ransomware compromise.
-
Use Volume Shadow Copy Service (VSS) to your advantage
In case you didn’t know, Shadow Copies represent Microsoft Windows’ feature for file backup. The operating system makes point-in-time snapshots of files over the course of critical updates and the creation of System Restore
points. Normally, the Zepto ransom Trojan disables VSS on early stages of the attack, but chances are it fails to.
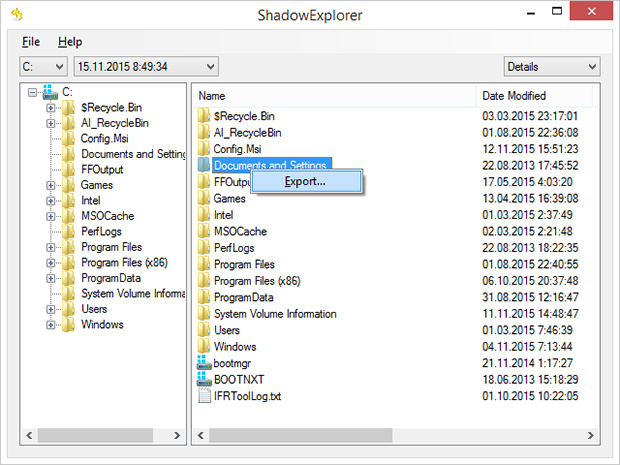
Nevertheless, it certainly won’t hurt to try this: for a start, download and install
Shadow Explorer
app. It is a free solution that displays the file hierarchy in a user-friendly way and automates the process of retrieving the previous versions of files and folders. You can easily export data by right-clicking the object
of interest and selecting the corresponding option as shown on the picture below.
-
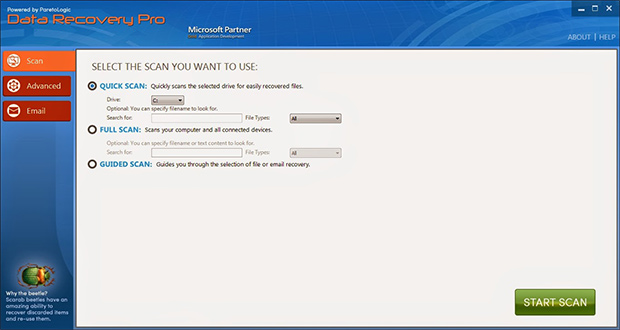
Try data recovery software
These types of solutions were originally designed for forensic purposes as well as to restore the information that was obliterated accidentally or due to hardware failures. Their scope of use has expanded with the emergence
of cryptographic infections like Zepto. Again, this isn’t a cure-all, but it may help under certain circumstances. So go ahead and download ParetoLogic’s Data Recovery Pro, have your computer scanned for recoverable
data and follow the program’s directions to proceed with the file rescue activity.
-
Use backups, they’re indispensable
Nothing beats backups when ransomware attacks your computer. No matter if your files are backed up to an external piece of hardware or a cloud provider, everything can be downloaded back to the machine in a few clicks. Just
make sure you have removed the ransomware before retrieving the data, otherwise the crypto routine will repeat.
Prevent ransomware attacks further on
In order to be a moving target for crypto malware like Zepto, it’s recommended to patch potentially vulnerable software (Adobe Flash Player, Java) on a regular basis, refrain from opening fishy email attachments, keep macros in
Microsoft Office documents disabled, use a dependable antimalware suite, and of course maintain secure backups of the most valuable files.
|

