|
Most ransom Trojans come and go, but only few stick around for months or even years. The ransomware called Locky falls into the latter category. Discovered in February this year, it has been on a steady upward curve in terms of
distribution ever since. Moreover, its makers appear to be constantly busy prepping new updates of their malady. In a recent move, the threat actors released an edition that the InfoSec community dubbed the Osiris ransomware.
This one arrives with spam, encrypts data with RSA-2048 and AES-128 cryptographic algorithms, and concatenates the .osiris extension to all mutilated files. The malicious code also cripples filenames so that the victim can no
longer work out which document, image, video, or database a certain .osiris entry corresponds to.
The attack is only complete as long as the felons’ demands are stated clearly. To this end, the infection creates ransom notes called OSIRIS-[random_4_chars].htm and DesktopOSIRIS.htm. These files are accessible with the victim’s
default web browser. According to these decryption walkthroughs, the user is supposed to install Tor Browser and enter a unique personal URL in it to visit Locky Decryptor page. The rest of the recovery workflow involves a payment
of the extorted ransom. The malefactors claim to provide the private decryption code and ad hoc tool in exchange for 0.5 Bitcoins. Of course, it’s up to every infected user whether they should pay or not, but this may turn out
to be a futile undertaking. Just like real-world criminals, cybercrooks are untrustworthy a priori.
The ne’er-do-wells at the helm of the Osiris (Locky) ransomware campaign still engage a botnet to spew out rogue emails with the malicious payload in them. As technically complex as this crypto threat is, it reaches computers
through commonplace social engineering. The spam emails may be disguised as invoices, ISP complaints, job offers and the like. The latest spam wave involves phishing emails titled “Amount Payable” that lures recipients into opening
the attachment. A lot of these unsafe files are Microsoft Word and Excel documents, which tell users to enable VBA macros and thus execute the ransomware.
Due to its fairly good cryptographic practices, the Osiris file virus is not decryptable for free. Meanwhile, paying the ransom is not an option for the overwhelming majority of infected users. The section below highlights a viable
trade-off between losing data and submitting digital cash to the attackers.
How to recover .osiris files without submitting the ransom
A brief disclaimer: the techniques described below do not actually decrypt the locked data. Instead, they provide viable workarounds for exploiting probable imperfections of the way that this virus implements the crypto and handles
the victim’s files. Although it’s premature to assert whether or not these tips will do the trick in your situation, nothing more efficient has been invented to date. Without further ado, peruse the following methods to mitigate
the harm from the ransomware compromise.
-
Use Volume Shadow Copy Service (VSS) to your advantage
In case you didn’t know, Shadow Copies represent Microsoft Windows’ feature for file backup. The operating system makes point-in-time snapshots of files over the course of critical updates and the creation of System Restore
points. Normally, the Zepto ransom Trojan disables VSS on early stages of the attack, but chances are it fails to.
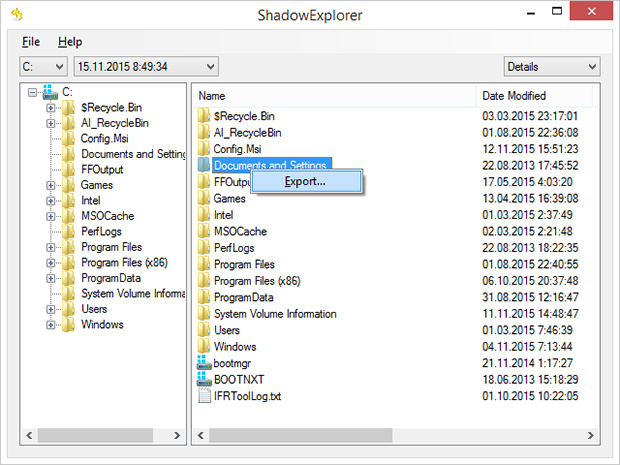
Nevertheless, it certainly won’t hurt to try this: for a start, download and install
Shadow Explorer
app. It is a free solution that displays the file hierarchy in a user-friendly way and automates the process of retrieving the previous versions of files and folders. You can easily export data by right-clicking the object
of interest and selecting the corresponding option as shown on the picture below.
-
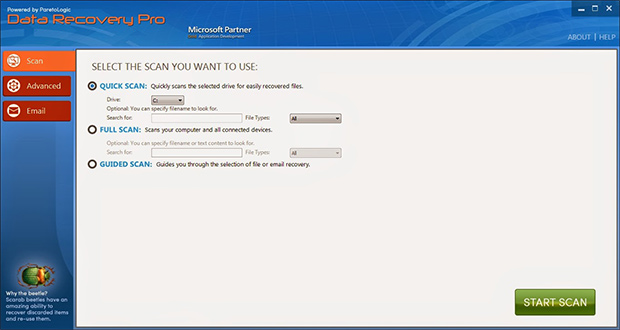
Try data recovery software
These types of solutions were originally designed for forensic purposes as well as to restore the information that was obliterated accidentally or due to hardware failures. Their scope of use has expanded with the emergence
of cryptographic infections like Osiris. Again, this isn’t a cure-all, but it may help under certain circumstances. So go ahead and download ParetoLogic’s Data Recovery Pro, have your computer scanned for recoverable
data and follow the program’s directions to proceed with the file rescue activity.
-
Use backups, they’re indispensable
Nothing beats backups when ransomware attacks your computer. No matter if your files are backed up to an external piece of hardware or a cloud provider, everything can be downloaded back to the machine in a few clicks. Just
make sure you have removed the ransomware before retrieving the data, otherwise the crypto routine will repeat.
Prevent ransomware attacks further on
In order to be a moving target for crypto malware like Osiris, it’s recommended to patch potentially vulnerable software (Adobe Flash Player, Java) on a regular basis, refrain from opening fishy email attachments, keep macros
in Microsoft Office documents disabled, use a dependable antimalware suite, and of course maintain secure backups of the most valuable files.
|

